Recently, I was going through my LinkedIn feed and I found a post by Jake M.
In the post, the author suggests a way to bypass Cloudflare’s protection and directly access the origin server. They propose using the ‘Forgot Password’ feature of a web app to find the server’s IP address. If that fails, they recommend sending an email to a non-existent address to receive a bounce notification with the server’s IP. That will expose the server IP and it’s possible to bypass Cloudflare’s security measures unless additional restrictions are in place.
Here’s how both scenarios can be visualized:
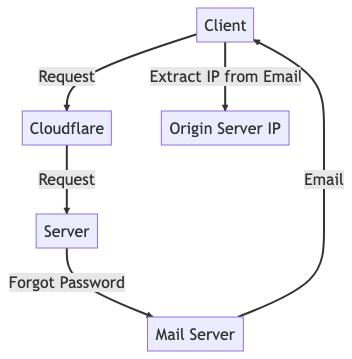
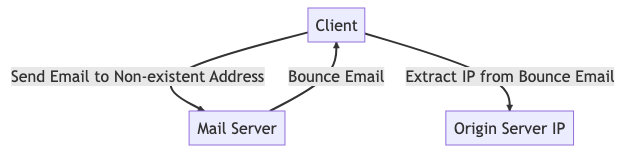
The author’s research very well points out a configuration vulnerability that is really difficult to visualize. If the Origin Server IP is exposed, there is no point in having CloudFlare. And this is the same issue with any Cloud Firewall / CDN that works in Proxy mode.
Suggested Workaround
As suggested in the comments, the most popular workaround would be to use a 3rd party email server. In that way when the mail server’s IP address is exposed, the Origin Server IP is still hidden behind the proxy.
However, what if someone wants to use the mail server on the same server? Is there no way out?
Actual Workaround – Bypass Prevention
Let’s look at the situation from a different perspective.
Our Origin Server IP is exposed via a mail server. We may circumvent this issue by moving the mail server out of our hosting infrastructure.
But the fact is, there might be more than one way to expose the Origin Server IP! And we may not have discovered all of them, while attackers might have. So it’s best to assume that the IP will be exposed anyway, and work on a strategy that prevents any incident based on the exposure. The solution can be called ‘Bypass Prevention’.
Bypass Prevention is very simple – we disable direct IP access to the web application hosted on the server. To do that, we need to simply restrict the access to IP range of CloudFlare.
For that, we need the current Cloudflare IP ranges list. Visit the Cloudflare IP Lists page or utilize their API to obtain the latest IP range list.
Once we have the list, we can use the .htaccess file to provide Bypass Prevention functionality.
To configure IP restrictions in the .htaccess file, follow these steps:
- Create or edit your .htaccess file in the root directory of your website.
- Add the following lines to the file:
# Block direct access to all files except from Cloudflare IPs
<Files *>
Order Deny,Allow
Deny from all
# Whitelist Cloudflare IP ranges
Allow from 103.21.244.0/22
Allow from 103.22.200.0/22
# Add more IP ranges here if needed
</Files>
- Replace the example IP ranges (
103.21.244.0/22and103.22.200.0/22) with the actual Cloudflare IP ranges you obtained from the sources mentioned earlier. - Save the .htaccess file.
These rules will deny access to all files on the website for requests from IP addresses outside the specified Cloudflare IP ranges. Only requests originating from Cloudflare IPs will be allowed.


